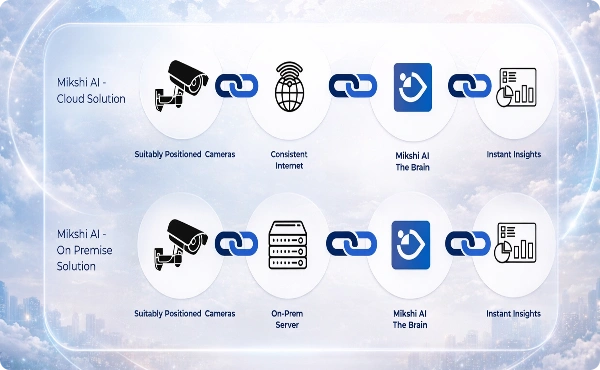
Turn Cameras Into Intelligent Access Monitoring Systems
Mikshi AI analyzes live camera feeds to monitor entry into defined restricted areas and detect unauthorized presence. All access events are centrally analyzed and delivered through dashboards, alerts, and reports—enabling real‑time enforcement and consistent access governance across sites.
Centralized Restricted Area Monitoring: Track access violations across facilities, buildings, and zones from a single dashboard.
Real‑Time Unauthorized Access Alerts: Instantly notify security or operations teams when restricted zones are breached.
Automated Access Violation Reports: Generate time‑stamped reports with visual evidence for audits and investigations.
Multi‑Site Access Governance: Enforce consistent access rules across locations, departments, or facilities.