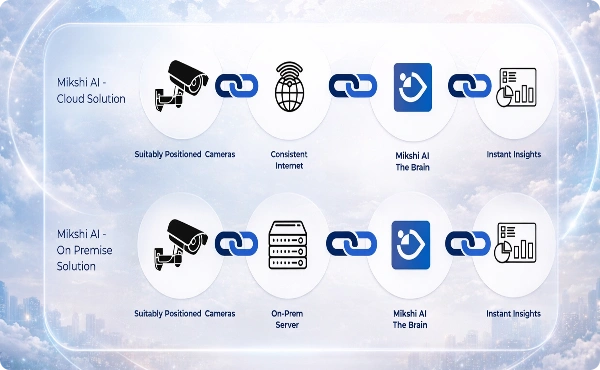
Turn Perimeter Cameras Into a Proactive Security Layer
Mikshi AI continuously analyzes live video feeds from perimeter cameras to detect unauthorized movement, fence breaches, or boundary crossings. All intrusion events are centrally analyzed and delivered through dashboards, alerts, and reports—enabling immediate response and consistent perimeter security across locations.
Centralized Perimeter Analytics: Monitor intrusion attempts, breach locations, and patterns across all sites from a single dashboard.
Real-Time Alerts & Notifications: Instantly notify security teams when perimeter intrusion is detected.
Automated Incident Reports: Generate time-stamped reports with visual evidence for investigations and audits.
Multi-Site Perimeter Governance: Enforce uniform perimeter security policies across facilities, campuses, or infrastructure sites.